Device Attestation
Device Attestation is used to verify whether the Commissionee is a genuinely certified product.
During the commissioning process, a device cryptographically attests to the Commissioner that:
it is a genuine product
it is a product that passed Matter compliance tests and has been thus certified by the Alliance
In order to accomplish those goals, the device carries:
DAC (Device Attestation Certificate)
Private key that matches the DAC
PAI certificate (Product Attestation Intermediate certificate)
Verifier
CD (Certification Declaration)
During the development phase, the manufacturer is able to test their devices without the full Attestation process. Testers should be explicitly informed that the device is under testing, and it hasn’t yet been certified and launched. Once a manufacturer enters a production phase, the ecosystem of the provisioner should enforce all Attestation requirements.
Attestation uses a Public Key Infrastructure (PKI) that leverages Root Certificate Authorities and Intermediate Certificates, in a similar way to the widely adopted server authentication certificates used for SSL/TLS. This process is called the Device Attestation Certificate Chain.
Device Attestation Public Key Infrastructure
In the device attestation PKI of Matter, root certificates are issued by multiple root CAs. Root CAs, also known as Product Attestation Authorities, are subject to strict scrutiny by Matter and the CSA. This is similar to the Web PKI used by browsers, but in this case, browsers and operating systems may include hundreds of root certificates from dozens of certification authorities in their default trusted root stores, while the numbers for matter device attestation PKI are much lower in both respects.
Each element of the PKI certificate chain starts with a PAA (Product Attestation Authority) and ends with a DAC. A complete device attestation PKI certificate chain always contains three certificates: PAA, PAI, and DAC, as shown in the diagram below.
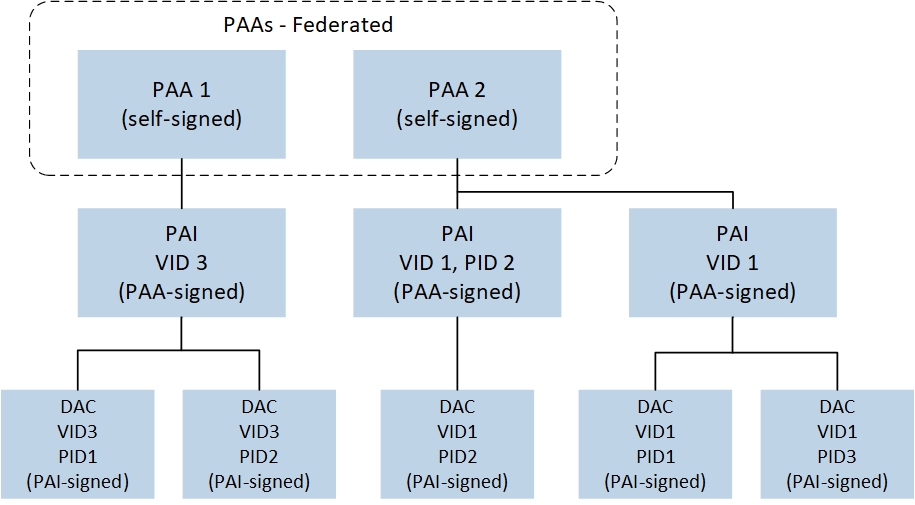
Device Attestation PKI
PAA: PAA is the root certificate in the chain, and it is self-signed. It includes:
Version
Serial Number
Signature
Issuer
Validity
Subject
Public Key
PAI: The PAI is signed by the PAA. It includes:
Version
Serial Number
Signature
Issuer
Validity
Subject (includes VID in MatterDACName)
Public Key
DAC: The DAC is signed by the PAI, and the PAA does not directly sign any DAC. Each Matter device's DAC is unique and associated with a unique attestation key pair within the product. It includes:
Version
Serial Number
Signature
Issuer
Validity
Subject (includes VID and PID in MatterDACName)
Public Key
Device Certification Declaration
A Certification Declaration (CD) is a cryptographic document that allows a Matter device to assert its protocol compliance. It is encoded in a CMS format described in RFC 5652. Upon successful completion of certification by a device type, Connectivity Standards Alliance creates the CD for that device type so that it can be included in the device firmware by the manufacturer.
The CD includes among other information:
VID
PID: This field contains an array of Product IDs (PIDs) that are covered by the same certification
Device Type: For example, 0x000a, which indicates that the device has the primary functionality of a door lock device type
Certification ID: Contains a globally unique sequence number assigned by the CSA to this CD
Security Level: Reserved
Security Information: Reserved
Version Number: The version number assigned by the CSA
Certification Type: Contains the type of certification for this CD
0: Development - used for development and testing
1: Provisional - for devices undergoing certification testing, or to allow production and distribution to occur in parallel with certification
2: Official - allocated after passing certification
Device Attestation Procedure
The device attestation procedure consists of the following steps:
The CertificateChain Request command is used by commissioner to read the device attestation certificate chain of a commissionee. Since the certificate chain of the commissionee includes two certificates (PAI and DAC), it typically requires two commands to obtain these two certificates.
The commissionee returns the CertificateChain Response command to reply to the commissioner with the requested certificates.
After obtaining the certificate chain, the Commissioner generates a random 32-byte attestation nonce.
The Commissioner sends the AttestationNonce to the Commissionee and request Attestation Information using AttestationRequest.
The Commissionee creates Attestation Information.
The Commissionee returns the signed Attestation Information to the Commissioner using AttestationResponse.
The Commissioner perform Attestation Information validation.
The procedure is illustrated in the picture below:
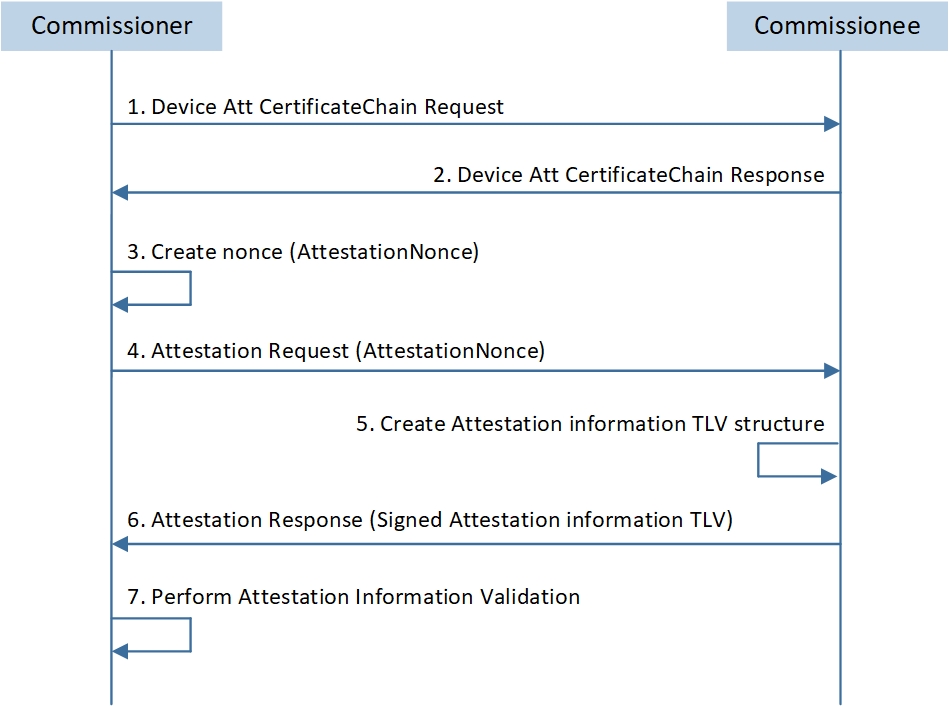
Device Attestation Procedure
In Step 7, the commissioner will verify the certification information using the following methods:
The PAA must be checked to ensure it is in the Commissioner's trusted root store, which should include at least the set of globally trusted PAA certificates present in the DCL (Distributed Compliance Ledger). For more information about the Distributed Compliance Ledger, refer to Distributed Compliance Ledger.
The DAC certificate chain is valid, including revocation checks of the DAC and PAI.
The VID of the PAI, DAC, and CD match. If the VID is included in the PAA, it should match the other certificates.
Validate the Device Attestation Signature (attestation_signature) field from Attestation Response.
The AttestationNonce in Device Attestation elements matches the Commissioner's provided AttestationNonce.
The Certification Declaration signature must be validated using the public key obtained from the CSA's Certificate Authority Certificate.
The Certification Declaration SHALL be validated.